Public Key Encryption with Public-Verifiable Decryption Delegation
Abstract
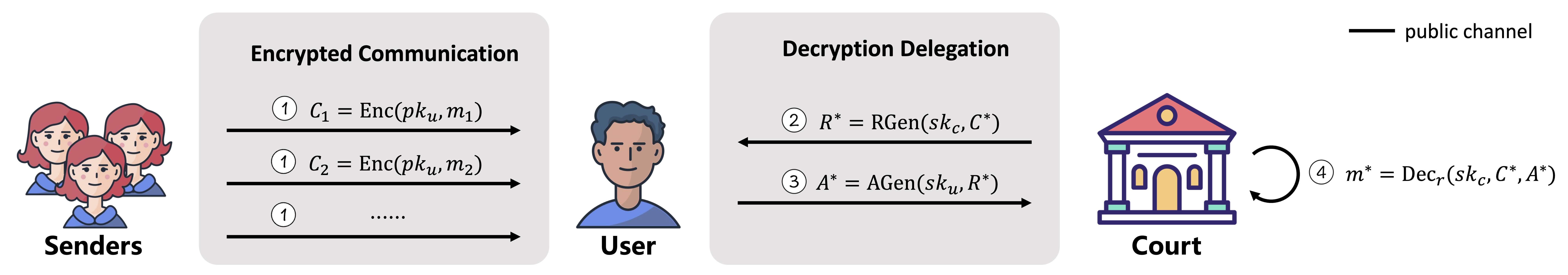
We introduce a new cryptographic primitive called public key encryption with public-verifiable decryption delegation ($PKE$-$PVD^2$), which allows the original decryptor to transmit the decryption key for a specific ciphertext to a designated recipient in a public-verifiable and privacy-preserving way. Due to its public-verifiable and ciphertext-level decryption delegation, it is helpful in the scenario requiring the special decryption delegation. For instance, the court needs to retrieve the specific message from the ciphertext as significant judgment evidence. Furthermore, by using the bilinear pairing, we present the first $PKE$-$PVD^2$ scheme and the corresponding security proof in the random oracle model. We also give a prototype of the proposal, and the extensive experimental results demonstrate the effectiveness and efficiency of our proposal.
Definition
- Setup$(\lambda)\rightarrow Para$: It takes a security parameter $\lambda$ as input and outputs the system parameter $Para$.
- KeyGen$(Para) \rightarrow (pk,sk)$: It takes the system parameter $Para$ as input and outputs a public/private key pair $(pk,sk)$.
- Enc$(pk_o, m) \rightarrow C$: It takes the original decryptor's public key $pk_o$ and the message $m$ in the message space as input and outputs a ciphertext $C$ of $m$.
- PrfGen$(sk_r,C)\rightarrow R$: It takes the designated recipient's private key $sk_r$ and the ciphertext $C$ as input and outputs the transmission request $R$ on $c_1$.
- PrfVrf$(pk_r,C,R) \rightarrow 1/0$: It takes the designated recipient's public key $pk_r$, the ciphertext $C$, and the transmission request $R$ as input and outputs $1$ if $R$ is a valid transmission request on $c_1$, or $0$ otherwise.
- AuthGen$(sk_o,R) \rightarrow A$: It takes the original decryptor's private key $sk_o$ and the transmission request $R$ as input and outputs the authorization information $A$ on $c_1$ if PrfVrf$(pk_r,C,R) \rightarrow 1$.
- AuthVrf$(pk_o,R,A) \rightarrow 1/0$: It takes the original decryptor's public key $pk_o$, the transmission request $R$, and the authorization information $A$ as input and outputs $1$ if $A$ is a valid authorization information on $c_1$, or $0$ otherwise.
- Deco$(sk_o,C) \rightarrow m$: It takes the original decryptor's private key $sk_o$ and the ciphertext $C$ as input and outputs the message $m$ or a special reject symbol $\perp$ denoted failure.
- Decr$(sk_r,C,A) \rightarrow m$: It takes the designated recipient's private key $sk_r$, the ciphertext $C$, and the authorization information $A$ as input and outputs the message $m$ or a special reject symbol $\perp$ denoted failure.
- Sign$(sk_o,m) \rightarrow \sigma$: It takes the original decryptor's private key $sk_o$ and the message $m$ in the message space as input and outputs the signature $\sigma$ for $m$.
- Vrfy$(pk_o,m,\sigma) \rightarrow 1/0$: It takes the original decryptor's public key $pk_o$, the message $m$, and the signature $\sigma$ as input and outputs $1$ if $\sigma$ is a valid signature for $m$, or $0$ otherwise.
Application in court scenario
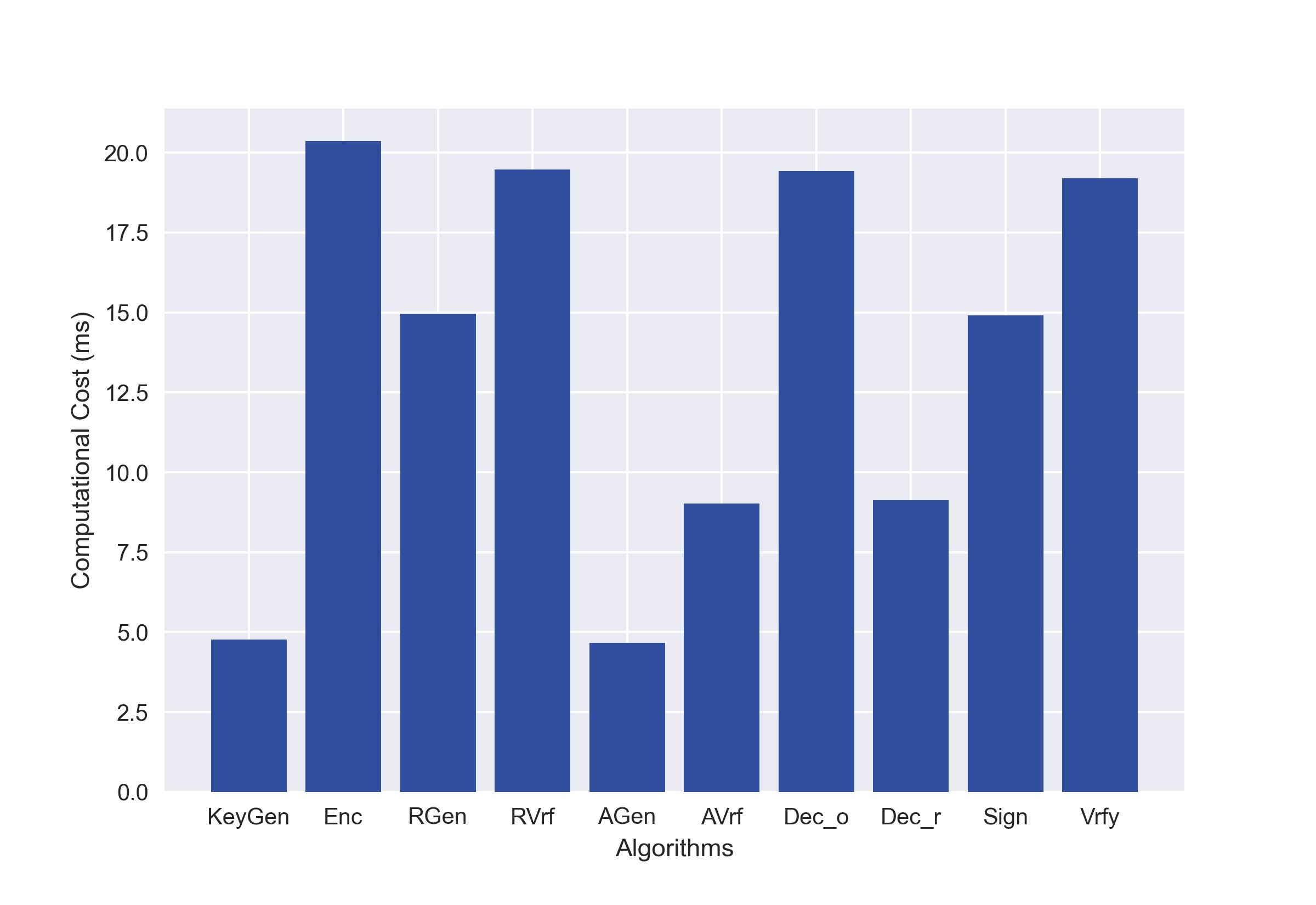
Performance evaluation
Demo download
The sourcecode of this project can be found at github.com/Archer-One/PKEPVDD_DEMO.